On the wave of the global attack of the virus-extortionist WannaCry, which occurred a week ago, there were questions - why did virtual criminals cope with it and how to deal with them. Hi-Tech Mail.Ru with the help of a young specialist sorted out the problems of cybersecurity as a blockchain and in the fate of the digital economy.
The largest in the history of the cyberattack of the WannaCry virus damaged the finances and reputation of companies in 70 countries, including Russia. "Megafon" and the Interior Ministry have been affected.
To understand the reasons for the "holes" in the protection of giants and to learn the future of the digital world, Hi-Tech Mail.Ru turned to the participant of MEPhI project "Business Incubator" and the former student of MEPhI Department of Cryptology and Cybersecurity Kirill Budnitskiy.
Kirill together with two co-workers has created and developed SNEG platform for safe and fast digital identification. The development combines a new method of encryption, access control, and blockchain. The authors of the project developed their platform architecture for quick and safe operation in the net.
Kirill Budnitskiy explained why, bearing in mind recent events, the development of the three programmers is a kind of solution to the problem of viruses-extortionists.

Kirill Budnitskiy. A photo from a personal archive.
Attack was training, and modern defense is all about holes
I'm surprised why such a massive attack of cryptoclockers (viruses-extortionists) did not happen before. I am sure that the attack on May, 12 was a training session – something bigger is being prepared.
Positive Technologies Company conducted 100 pentests on a hundred Russian companies. The report is on the site, you can see - only two companies have detected penetration and only in one case they began to react to this!
Now the security is actually zero. The means of protection are not updated, the threats are ignored. Attack is perceived as something ephemeral. Everyone thinks: "This will not happen to me". And the statistics says something else.
According to the FSB, last year 70 million targeted cyberattacks have been made on Russia. This is 2.5 attacks per second.
In addition, anti-virus protection is working "fifty fifty". That means, they can work, or they can not. And attempts of defence look like a lone turnstile in the middle of a spacious corridor.
Anyone can become a hacker
The WikiLeaks website has malicious software and is accompanied by a user's guide. If you read it, set up VPN carefully through the proxy, you can attack anything you want.
Everyone can "hack" and be hacked. For example, anyone can copy the code of a simple cryptolocker and start it. Not even extorting money, just for fun.
Malware programs, viruses and hackers are always one step ahead. They quickly adapt, bypassing the protection against them. And big companies are too slow to react to such a rhythm.
In case of an attack, you need to know where you have a hole in order to block it or isolate the source. And secondly, you need to have backup copies of the data.
Do not "store eggs in one basket"
With a distributed storage system, the attack of cryptolockers is not terrible. Not that it provides protection. But if your access to documents is blocked and someone is extorting money, you do not lose any data - they are in a copy.
There is, say, a Word document. It belongs to you, is stored on your computer. In encrypted and replicated form it is stored in a system of, for example, five nodes, that is, five computers.
Other computers may not even know what they are storing. And if they find a document and decide to somehow decipher it, the system will find out. Then it will say: "This node is infected." It is isolated, deprived of rights and "treated".
It's as if there were five people in the room. Everyone would say “yes”, but one would say “no, no, no”. And the other four would have thought something is wrong with him.
Here is a cryptoclocker attacking. The data is encrypted by the virus, and it begins to extort money. But the threat of losing data is not terrible to you, as well as blackmailing. Destroy the system. Everything will be easily restored then.
The distributed database will save the documents. The computer downloads them as you download photos from Google Drive.
This is a key feature of a distributed database - information is not only stored in blocks in different places, it is also replicated. It ensures the integrity of information and its easy recovery.
Cyberwar will end, never having begun
One of the ideas of our platform is the provision of a distributed database. It is created on the basis of the distributed registry. This is essentially a blockchain. If we explain in a very simple language, the blockchain is a chain of hashes.
Blocking is the basis for digital transactions in the digital world and in the digital economy.
Alisa had 20 rubles - bitcoins in the digital world. She transferred them to Bob, and her virtual wallet was empty. Then Alice decides to transfer 20 bitcoins to Eve - the same 20 rubles, which are no longer there. And the system remembers that Alice once transferred 20 bitcoins to Bob, and new money did not appear.

Kirill has been seriously engaged in issues of cybersecurity and the creation of distributed databases since February. Photo is from his personal archive. Forum Breakpoint
The system remembers the transactions made - from the first to the last. It blocks Alice's attempt to transfer non-existent money, because it sees the same hash.
The principle excludes fraud in any form, whether it is an attempt to steal money, interferance with the user's attributes (personal data) or change of some information that can be used in cyberwar.
The future of the digital economy
Such a system excludes fraud, it reduces transaction time, financial costs and even brings profit to users. It is an open system, in which digital technology is used in everyday life.
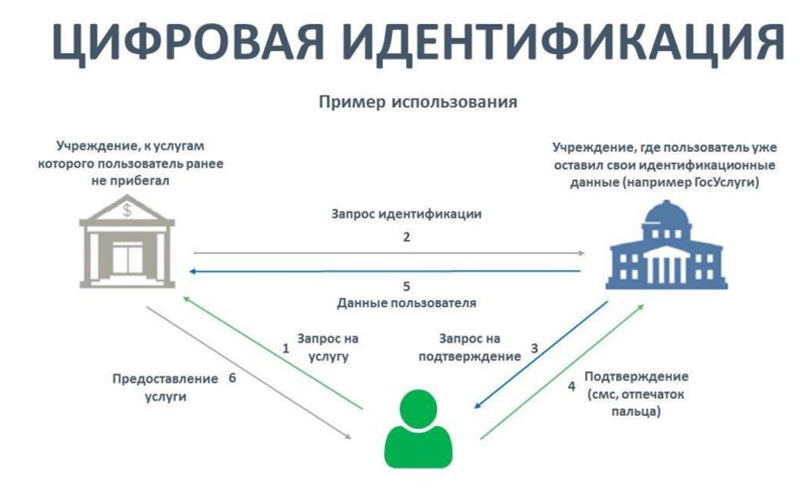
The concept of transactions has become wider. It went beyond the financial sector, and is now applicable in the legal environment. For example, when requesting the receipt of personal data of a person.
You applied to a bank that you did not use before. The bank needs to verify your identity. It makes a request to the state institution, from there comes an authentication request in any way - SMS, fingerprint.
Digital identity is working as an automatic intermediary or virtual arbitrator based on the distributed registry. This eliminates the loss of data or its distortion due to errors, speeds up operations, solves the problem of scalability.
This allows the bank to enter a new level of lending, when a guarantor is not needed, and for the company - to reach the target customer service. And, for example, if you enter government structures, you can literally keep track of what taxes have gone into.